Authorization and Authentication Process: 5 Ways to Fix Security Gaps

If Rip Van Winkle were to wake up today from his 20 year sleep, he would consider this a magical world. While technology has made our lives easier, faster, better and more fun, the thieves of Rip Van WInkle’s world have moved online today. And Authorization and Authentication are part of the security detail that is aiding in putting up a strong fight. One report by KPMG claims that cyberattacks cost businesses an estimated $400 billion a year. And what is more concerning is that the insurance industry appears to be a growing target for cybercrimes.
Insurance data is a goldmine for cyber criminals
Your average insurance company sits on a mountain of sensitive user information that is a virtual goldmine for hackers. Thousands of user’s bank details, addresses, phone numbers, and more are stored in insurance databases.
Most banks have ramped up their security measures, so the next best way to access user’s bank accounts is to commit identity theft using information stolen from insurance companies. A breach in data security through unauthorized access will not only affect your credibility as a company, but will also see you on the wrong side of stringent data protection acts.
When it comes to securing your data with identity management solutions, there are three main areas that you need to think about:
- Who can access your data?
- How do you verify their identity?
- How do you block unverified access requests?
To answer these questions, we first need to understand the real meaning behind the commonly used terms: authorization and authentication.
Authentication vs Authorization
Authorization and authentication are two terms that are often used interchangeably. However, the processes and implications behind them are extremely different.
Authentication is the process of verifying the identity of a person, i.e. confirming you are who you say you are.
Authorization is the level of access that is provided to a person once they are authenticated.
To understand it in a simpler way, think about the last time you checked into a hotel. You show your ID card to the receptionist at the lobby to confirm your identity. Once they verify it, they hand you your room keys, which means you can enter the hotel, but only go into the room allotted to you.
Authorization and authentication in insurance systems work in much the same way. An agent enters their username and password to gain entry into the system, but once in, depending on their function, they can only access certain details within the dashboard.
Also Read: Best-of-breed vs Integrated Systems: Which is Right For Your Company?
Security gaps in authorization and authentication
Authorization and authentication are essential steps in all identity management solutions. But there are multiple ways of doing them, and not all are made equal. Take for instance, the most common authentication process: entering a username and password. It’s how you access your email and most likely, how your agents enter their dashboards. But a vast number of passwords are weak and can easily be replicated by hacking software algorithms.
You don’t need to look further than the most popular password of 2020 -12345- to know that passwords aren’t always the foolproof barrier we like to think they are. When it comes to authorization too, unless your access levels are well-defined and protected, users can break through them and access restricted information. Newer features like self-service, provide access to insurance policy holders, making it all the more important that your identity and access management system is watertight.
Critical insurance security features
To prevent unauthorized access and to remain on the right side of data protection acts, there are five security measures that your identity and access management software needs to have:
-
OAuth Identification
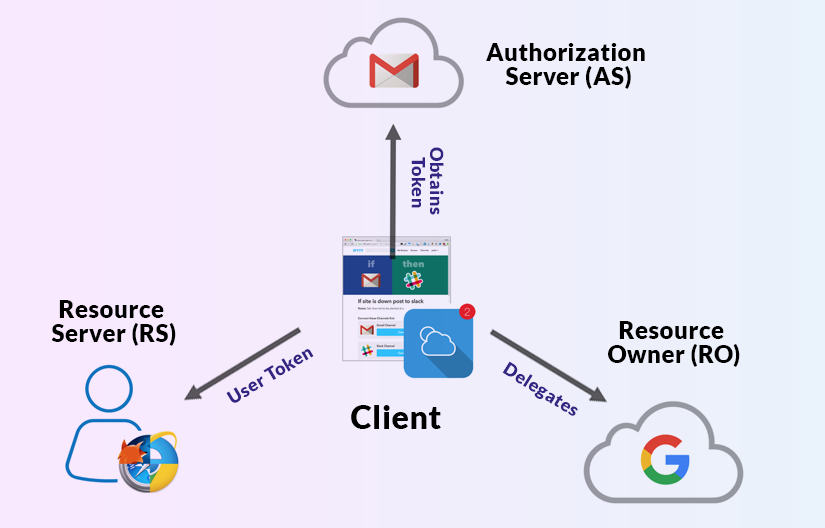
Most platforms today are developed for interoperability. Your social media account, for instance, may connect with your digital wallet, your messaging app, and other personal applications. Similarly, your insurance software may connect to your CRM and internal HR portal. If in this scenario, a user had to enter their username and password for each of these platforms, a hacker could tap into the weakest link and access the credentials.
OAuth identification is one of the most secure identity management solutions that circumvents this flaw entirely. In this two-step authentication process, when you connect the credentials of one platform with another, you provide a valid web token which is passed between both platforms. Once the other platform validates the web token, you can gain entry. Since there are two steps to authentication, this method is known as multi-factor authentication.
The most important feature of OAuth identification is that only you can provide a valid web token, not a hacker or a hacking software. Therefore, it’s virtually impossible to hack into your information with multi-factor authentication.
-
End-to-end data encryption
Transmission of data between platforms or between applications and cloud servers needs to be encrypted. While most insurance software does offer encryption, it’s important to note that not all forms of encryption are equally secure.
The SHA-256 cryptographic hash is currently one of the most secure forms of encryption. Personally Identifiable Information (PII) is the most protected data in insurance and is subject to strong compliance standards. Your insurance software needs to ensure that this data isn’t just encrypted when being exchanged between platforms, but also when it is stored.
-
Secure code
An insurance software is only as secure as the framework it is built on. The framework is essentially the very foundation of the software. If there are weak links in the framework, then any additional security features you add to it will not be effective.Application leaders must anticipate and prepare to mitigate potential risks of data corruption, model theft, and adversarial samples. - Gartner
To ensure that the framework continues to be secure, Insurtech solutions like SimpleSolve run periodic VAPT (Vulnerability Assessment and Penetration Testing) audits to identify any weaknesses in the code and resolve them before they become a security liability. -
Multi-level authorization
Your insurance software needs to have several levels of role-based authorizations to ensure sensitive information doesn’t fall into the wrong hands. Depending upon your setup, you will need separate access levels for agents in different departments, for supervisors and for top-level leadership. If you offer self-service for customers, then you will also need separate access for customers where they can only see their account-related information.
To simplify the process of role-based authorization, SimpleSolve offers roles defined by business functions instead of technical application objects. The role-based security model provides the insurance carrier the full capability of configuring roles that suit their individual business model.
-
Compliance with regulatory standards
Personally Identifiable Information (PII) is the most protected data in insurance and is subject to strong compliance standards. Your insurance software needs to ensure that this data isn’t just encrypted when being exchanged between platforms, but also when it is stored. This will protect you against any potentially damaging compliance violations.
A robust insurance software with two-step authentication and strong identity and access management features can give you and your customers invaluable peace of mind about the security of sensitive information. Mitigating cybersecurity threats will ultimately improve your organization’s ability to deliver superior customer service and satisfaction.
Want to know how else SimpleSolve can help with authentication and authorization? Our experts are available.




